Filters
Content Type
Topic
Cybersecurity Marketing 101: How to Plan and Execute a Winning Strategy
With the increasing reliance placed on computers in 2023, cybersecurity is quickly becoming one of the most in-demand industry niches. With the rise in demand comes a huge influx of new companies hoping to capitalize on the growth.
If you’re hoping to compete seriously with these companies, you’ll need a strong go-to-market strategy that incorporates winning principles at every stage of development. To help you hit the ground running toward profitability, we’ve put together today’s guide.
We’ll start by explaining how to find gaps in existing services you can exploit to develop your product, then we’ll cover how to market cyber security services and include some key examples you can use when just starting.
Let’s get started by discussing how you can study the market you plan to enter.
Analyzing Your Market
Before you can dive into product development, you’ll need to figure out whom you’re serving and what they need. In other words, you’ll need to find your why.
This illustration of Porter’s five forces analysis is one example of a market analysis strategy:
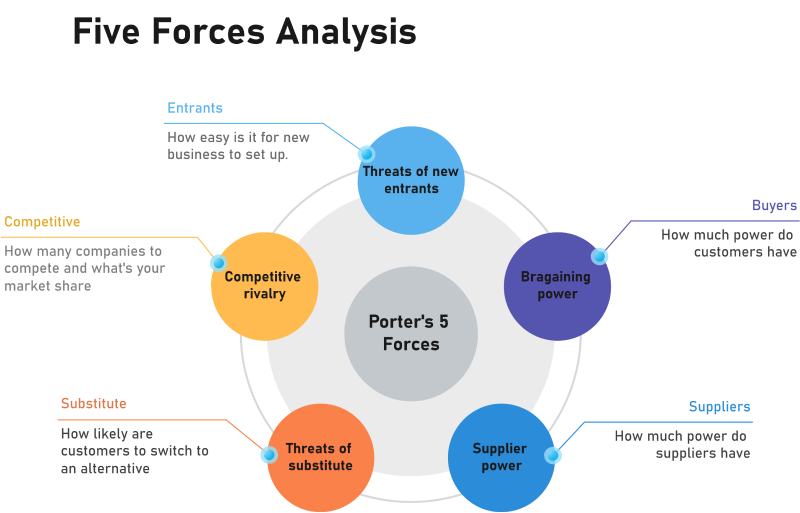
Here are a few more tips for analyzing your market:
Find the Pain Points
Look for common industry pain points that you believe you can address. Research your competition and look for problems they aren’t solving. These gaps are your best opportunities to enter the market.
The more acute these pains are, the easier it is to invoke them when speaking with potential customers.
Learn Your Target Audience
Become familiar with who the usual buyers in the industry are. If you’re targeting small businesses, you’ll need to get comfortable communicating with business owners without much technical knowledge. If your solution is geared toward medium and large businesses, you’ll be dealing with dedicated IT managers.
In either case, your approach, positioning, and marketing need to be tailored to these buyers.
Consider Specializing in a Single Vertical
As the world’s reliance on technology grows, so too do regulations and laws that apply to specific industries surrounding cyber security.
Some industries, like healthcare, have complex compliance standards which make choosing a cybersecurity solution more difficult.
Being able to offer a solution that can directly address important laws like HIPAA may be more valuable than a one-size-fits-all solution aimed at a wide audience.
Pick Your Pricing Model
There is no limit to the number of creative ways you can charge for your product. The best way for your company to turn a profit depends on factors like the sizes of businesses you’re targeting, who your buyers are, and the specific ways your solution provides value.
Here are a couple of examples of useful pricing models you can explore.
Per User Pricing Model
In a per user price model, your buyers pay based on the number of users that need access to your solution. This model is great for companies that provide SaaS solutions and fits in well with an annual or monthly subscription.
- Per user pricing is straightforward and easy to budget for, which makes it attractive to potential buyers.
- However, per user pricing means large organizations end up paying a lot more for your services, which could be a deal breaker for them.
Tiered Pricing
Under a tiered pricing model, you’d charge companies different amounts for different levels of service. Higher price points would come with more advanced products, features, and support.
- Tiered pricing models encourage customers to pay extra for full services and support. This helps them customize their package and pick the option which is best for them.
- However, tiered pricing can become complicated, especially if you offer several different tiers. It could also make it more likely that customers pay for products they don’t want or need.
Develop Your Marketing Strategy
It’s now time to develop cybersecurity marketing campaigns that will get your product in front of the right buyers at the right time.
At Hushly, we’re proponents of proven digital marketing techniques like account-based marketing (ABM) and content marketing. We believe the best way to attract high-value customers is through customized content that addresses every stage of your buyer’s journey.
Here are some examples of marketing strategies you can focus on that can generate demand and help turn leads into buyers.
Account Based Marketing
ABM is the practice of focusing on high-value accounts via targeted marketing materials. We believe ABM is the best way for cybersecurity firms to develop partnerships that result in strong relationships and long-term mutual growth.
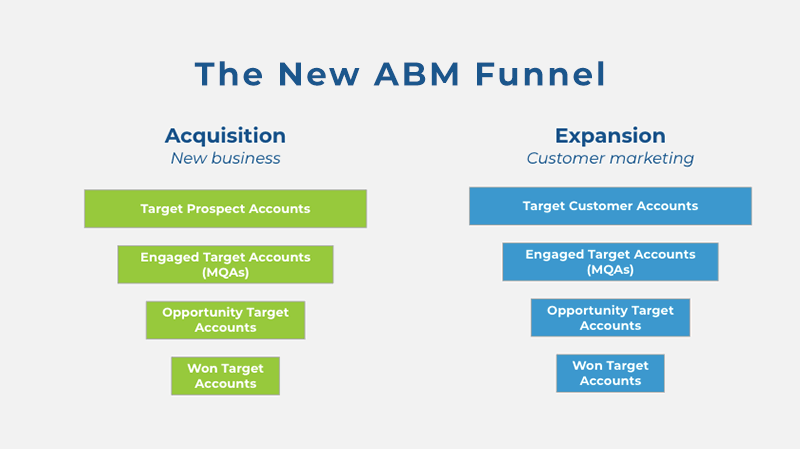
Here are a few tips for learning how to market cybersecurity services using ABM:
- Start with buyer personas to get to know your buyers and target them effectively.
- Create omnichannel content so your buyers always have answers at their fingertips no matter when or where they’re researching.
- Invest in a marketing platform that provides unique website experiences, customized landing pages, and detailed visitor analytics for each account on your list.
- Focus on providing value up-front. This generates trust and builds your authority with your targeted buyers, leading to increased conversions and better relationships.
Service Landing Pages
Consider creating dedicated landing pages for each of your products or services. These pages should highlight important features and benefits relevant to the buyers you’re looking to convert. Service landing pages are effective because they allow you to speak directly to the buyers you’re looking to target and present only the most relevant information to them.
For example, if your company has developed a new identity and access management (IAM) system, you could create a service landing page explaining how your solution provides increased security, full compliance within your chosen vertical, and reduced risk of data breaches.
Content Marketing (eBooks, Blogs, Whitepapers, etc.)
Cybersecurity content marketing is essential for companies looking to compete in 2023.
Your cybersecurity solution is complex. This means the value it provides is not always obvious to those without industry knowledge. Even to those within the industry, your solution may require in-depth research before buyers are comfortable closing deals.
To help with this, Hushly recommends a comprehensive inbound content marketing strategy that guides customers through every stage of the buyer journey.
Examples of inbound content you should create are:
- eBooks: introduce complex topics to a wide audience. They are also perfect opportunities to build authority and help your customers understand why your solution is valuable.
- Blogs: provide customers with up-to-date information on your services, industry developments, and trends in the cybersecurity world.
- Whitepapers: present an emerging cybersecurity problem and take a deep dive into your proposed solution. More detailed than both blogs and eBooks, an influential whitepaper could bring tons of traffic and even shift industry standards for years to come.
Hushly Takes the Stress of Marketing Off Your Shoulders
If you’re interested in breaking into the rapidly growing cybersecurity space, marketing is bound to be one of the most time-consuming and important aspects of your launch. Your company can’t afford to go too long before finding profitability, so getting your cybersecurity marketing campaigns right the first time is critically important to your burgeoning operation.
If you’d like a cybersecurity marketing agency with years of experience that helps firms like yours establish themselves and see rapid growth, Hushly can help.
Get in touch to see how Hushly can guide your cybersecurity marketing strategy and put you on the path toward growth.
The post Cybersecurity Marketing 101: How to Plan and Execute a Winning Strategy appeared first on Hushly.



